Security Questions
If you’ve ever forgotten a password, you know that many online sites offer the ability to recover a password by answering security questions. These are another area of vulnerability. Since these questions ask for information that is likely revealed on social media sites such as Facebook, they are a poor means of providing security. In fact, the security firm Kaspersky Labs recommends not directly answering these. You might respond to a question such as, “What was the name of the first pet you owned?” not with the correct response (“Fido”) but with something resembling a password: bh$4dp7.
Other Means of Identification
Two-Step Authentication
One way to protect yourself online is to take advantage of two-step authentication. This is available on some sites and many more will likely add it in the near future. Two-step authentication basically means having another device such as a smartphone or text-enabled cellphone to deliver a special one-time code for signing into a service. This of course assumes you have your device in your physical possession. This is another reason to have software such as Find My Phone or similar software on all your portable devices, including laptops.
Fingerprints
The use of passwords is not the only means for authenticating an individual. For more than 100 years, fingerprints have been used in the judicial systems to establish a person’s identity. Until recently, this technology wasn’t commonly used on personal computing devices. However, with the release of the iPhone 5s in September 2013, Apple introduced technology it calls Touch ID. This allows a person to unlock his smartphone using his fingerprint instead of typing in a passcode. As an iPhone 5s user, I can say it works flawlessly once it is set up. I have had numerous people attempt to fool the system, but none have been successful. Apple also allows Touch ID to be used for identification instead of a password for purchases from the iTunes Store. The Touch ID technology is now available to third-party
developers with the recent release of iOS 8. Many developers already have updated or are working to update their software to take advantage of this. Now some out there might be nervous about allowing a company access to your fingerprint, but the information is only stored locally on your device and is sandboxed so no other applications have direct access to the information.
Android devices have a similar option from Samsung. The recently released Galaxy 5s has fingerprint identification capabilities, as does the new Amazon Fire Phone. Samsung is also working with online payment system PayPal to incorporate biometric identification in the new Galaxy 5s for accepting mobile payments.
The use of fingerprints for identification should go a long way toward the goal of eventually eliminating passwords, but it will be some time before this happens. It wouldn’t be surprising to have similar technology built into laptops and available as a USB accessory for desktop computers. In science fiction and crime drama on TV, retina scans are commonly seen, and it might indeed be the technology of the future in addition to fingerprints as a sort of two-factor authentication.
Another new payment system, Apple Pay, should solve many problems involving credit-card purchases. It integrates with Touch ID to allow you to pay for merchandise at brick-and-mortar stores with just a single touch. This will also work with Apple Watch. More information on Apple Pay can be found at apple.com/apple-pay.
Steps You Can Take
If you are concerned about your personal security online, there are companies out there to help. One is LifeLock (lifelock.com). I am currently using its services for free due to one of the security breaches in which I was affected. I am sure there are others, but be sure to do some research before relying on one of them.
Even with a service such as this, you should still takes steps to make sure you don’t become a victim. Here are a few things you can do to protect yourself online:
- Use software to store you passwords.
- Use a private email address for logins.
- Always make sure you are using http s for all your web browsing.
- Use the guidelines given in this article for generating passwords.
- Don’t directly answer security questions.
- Keep your credit card information offline. Don’t allow companies to store that information.
- If available, take advantage of login notifications.
- Use two-step authentication whenever possible.
I think Apple CEO Tim Cook recently summarized it best in an interview with Charlie Rose: “How do companies make their money? Follow the money. And if they are making money mainly by collecting gobs of personal data, I think you have a right to be worried and you should really understand what’s happening to that data and companies should be transparent about it.”
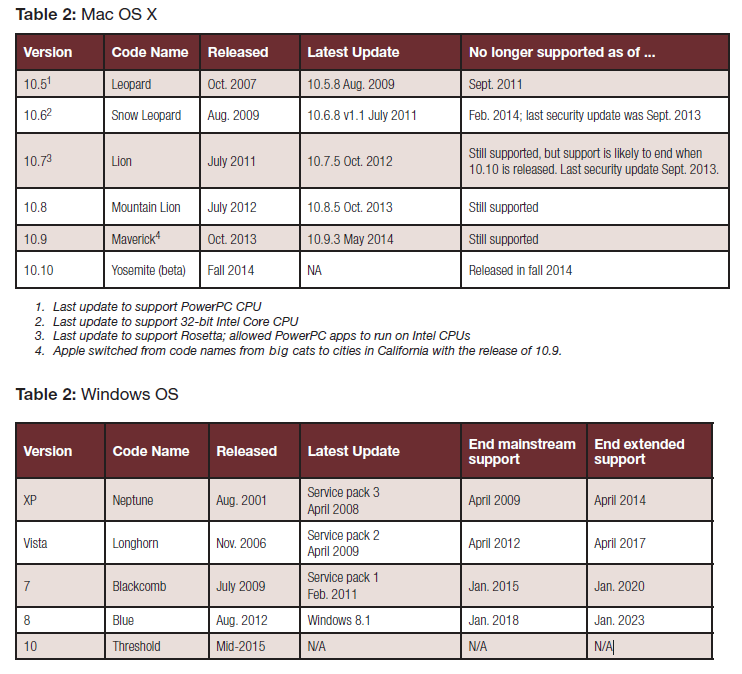
Windows and Mac Operating Systems
Another factor in online security is the computing platform on which you operate. Downloading the regular updates of your system software is the best way to guard against having your local personal information hacked. See the two tables below for the best software updates for the Mac OS and the Windows OS.